https://github.com/yeti-platform/yeti
Your Everyday Threat Intelligence
https://github.com/yeti-platform/yeti
dfir enrichment infosec intelligence threat-hunting threat-sharing threatintel
Last synced: 10 months ago
JSON representation
Your Everyday Threat Intelligence
- Host: GitHub
- URL: https://github.com/yeti-platform/yeti
- Owner: yeti-platform
- License: apache-2.0
- Created: 2015-12-13T16:54:26.000Z (about 10 years ago)
- Default Branch: main
- Last Pushed: 2025-05-01T22:27:42.000Z (10 months ago)
- Last Synced: 2025-05-01T22:31:16.504Z (10 months ago)
- Topics: dfir, enrichment, infosec, intelligence, threat-hunting, threat-sharing, threatintel
- Language: Python
- Homepage: https://yeti-platform.io/
- Size: 34.7 MB
- Stars: 1,846
- Watchers: 101
- Forks: 299
- Open Issues: 38
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-malware-analysis - YETI - Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified repository. (Open Source Threat Intelligence / Other Resources)
- awesome-threat-intelligence - Yeti
- fucking-awesome-malware-analysis - YETI - Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified repository. (Open Source Threat Intelligence / Other Resources)
- awesome-yara - Yeti
- awesome-csirt - Yeti - platform.github.io/) [Threat Intelligence](https://github.com/fr0gger/yeti) (Blue Team / Threat Hunting)
- awesome-hacking-lists - yeti-platform/yeti - Your Everyday Threat Intelligence (Python)
- Awesome-OSINT-For-Everything - YETI - Your everyday threat intelligence platform. (THREAT INTEL)
README
# Yeti Platform
Yeti aims to bridge the gap between CTI and DFIR practitioners by providing a
Forensics Intelligence platform and pipeline for DFIR teams. It was born out of frustration
of having to answer the question "where have I seen this artifact before?" or
"how do I search for IOCs related to this threat (or all threats?) in my timeline?"
Documentation links:
* Main website: https://yeti-platform.io/
* [Documentation](https://yeti-platform.io/docs)
* [Guides](https://yeti-platform.io/guides)
## What is Yeti?
In a nutshell, Yeti allows you to:
- Bulk search observables and get a pretty good guess on the nature of the
threat, and how to find it on a system.
- Inversely, focus on a threat and quickly list all TTPs, malware, and related
DFIR artifacts.
- Let CTI analysts focus on adding intelligence rather than worrying about
machine-readable export formats.
- Incorporate your own data sources, analytics, and logic very easily.
This is done by:
- Storing technical and tactical CTI (observables, TTPs, campagins, etc.) from
internal or external systems.
- Being a backend for DFIR-related queries: Yara signatures, Sigma rules, DFIQ.
- Providing a web API to automate queries (think incident management platform)
and enrichment (think malware sandbox).
- Export the data in user-defined formats so that they can be ingested by
third-party applications (SIEM, DFIR platforms).
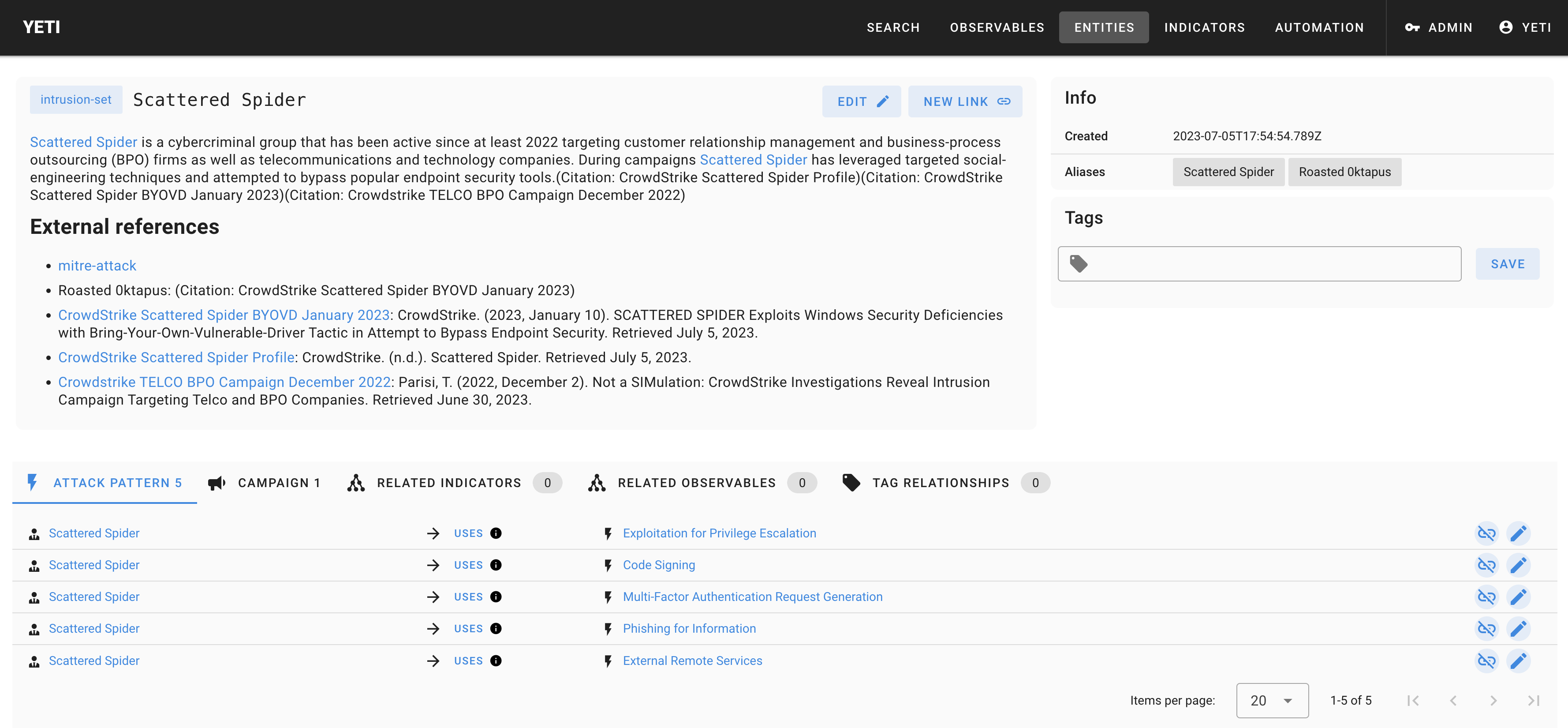
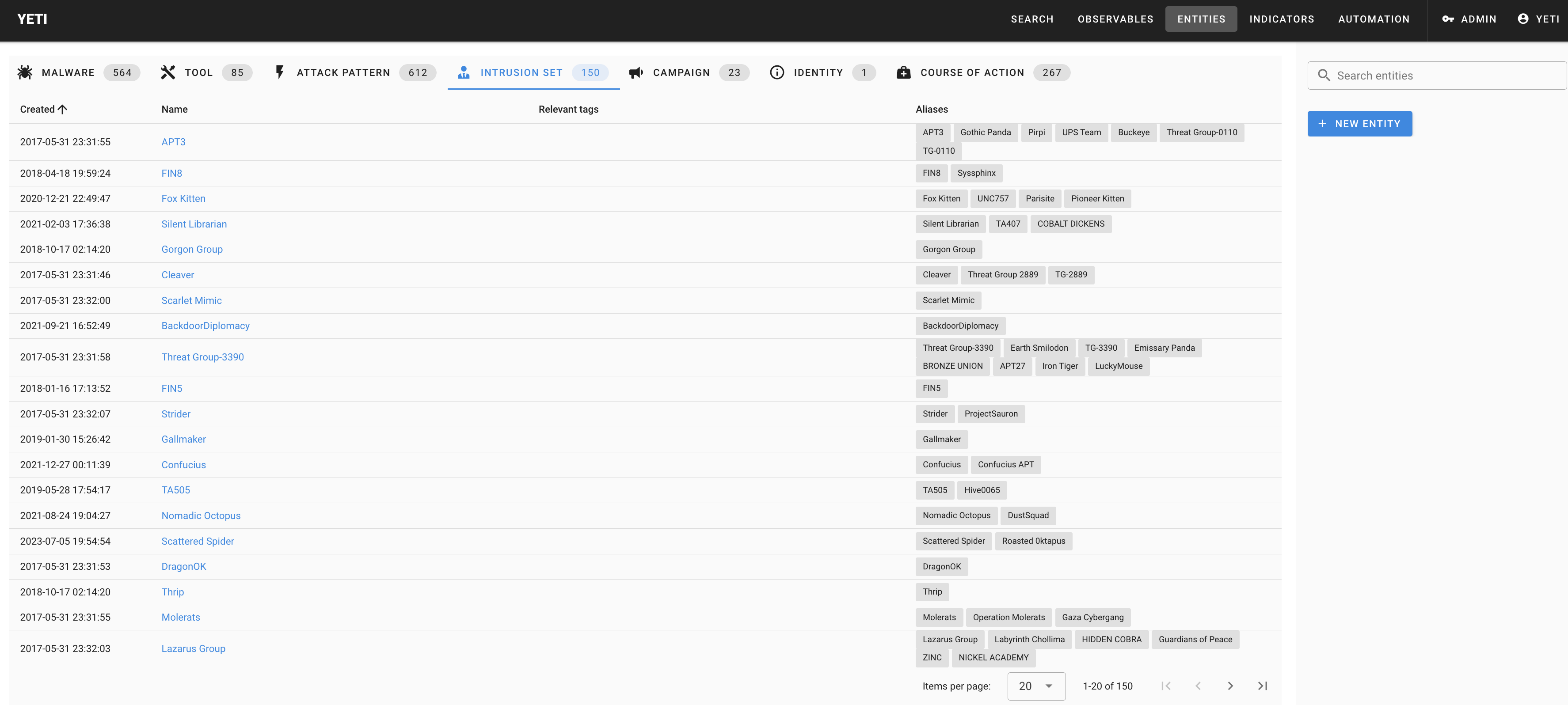
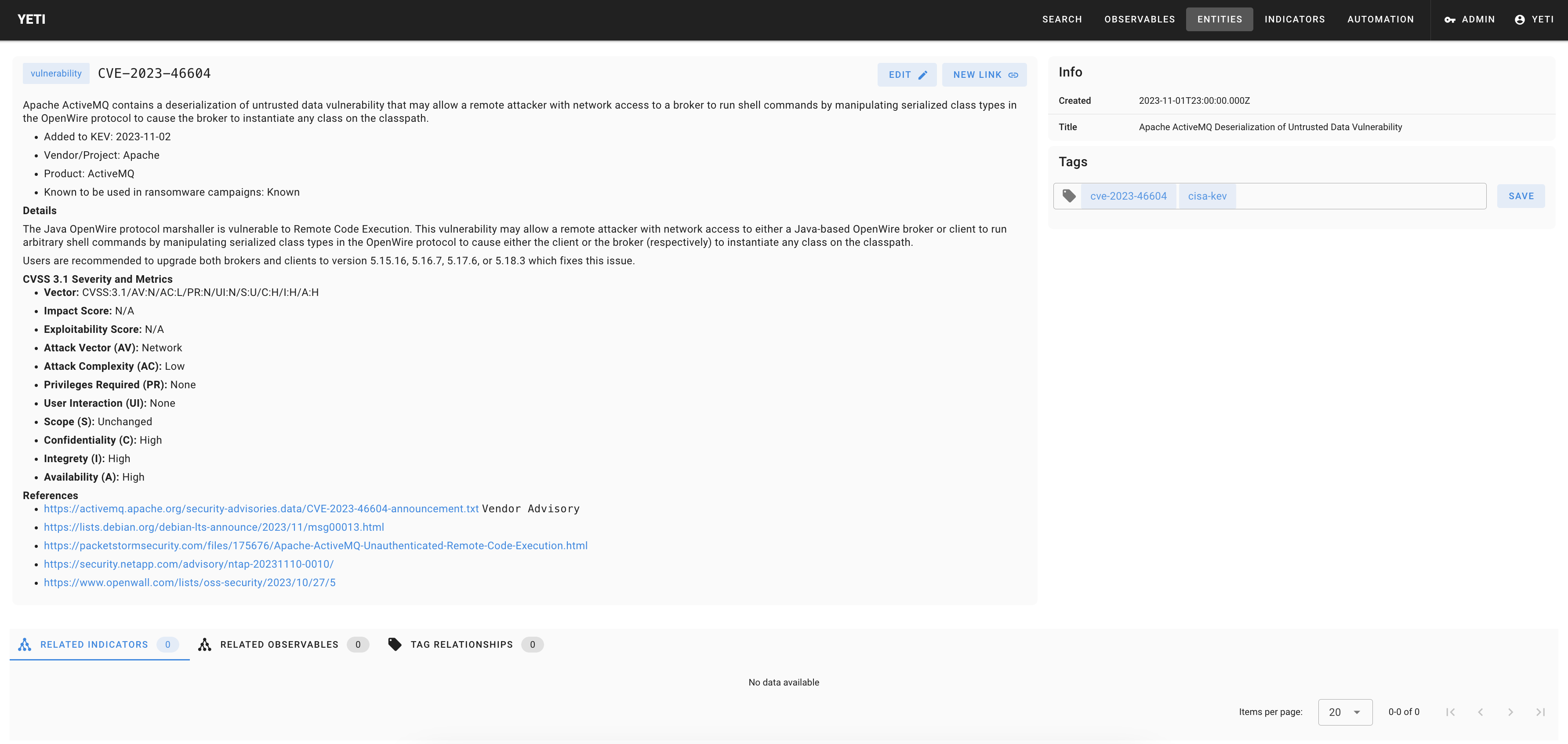
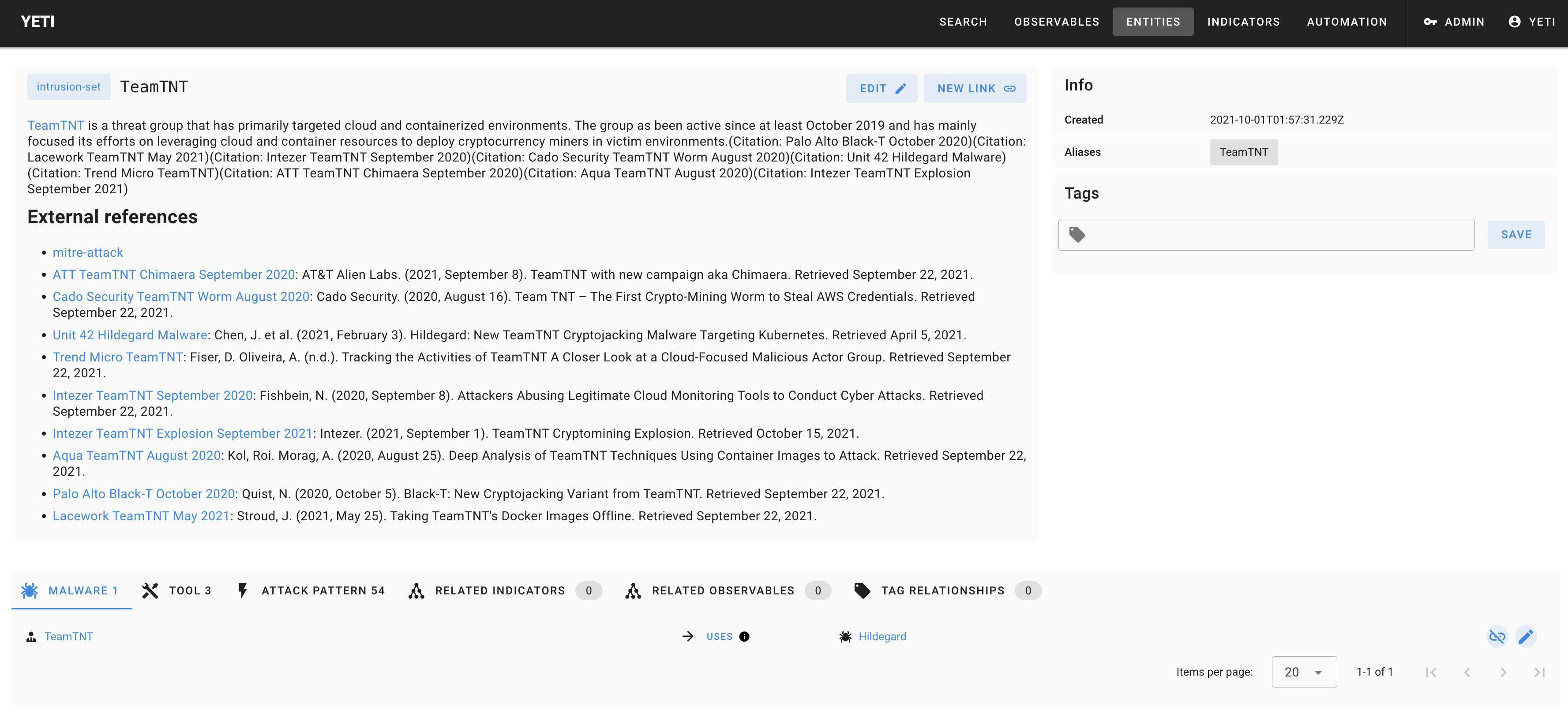
## Some screenshots