https://github.com/zarkones/onionc2
C2 writen in Rust & Go powered by Tor network.
https://github.com/zarkones/onionc2
adversary-simulation botnet c2 hacking onion pentesting red-team remote-access remote-control tor xena
Last synced: 4 months ago
JSON representation
C2 writen in Rust & Go powered by Tor network.
- Host: GitHub
- URL: https://github.com/zarkones/onionc2
- Owner: zarkones
- License: other
- Created: 2025-05-25T18:32:34.000Z (5 months ago)
- Default Branch: production
- Last Pushed: 2025-06-21T14:05:20.000Z (4 months ago)
- Last Synced: 2025-06-21T15:21:34.491Z (4 months ago)
- Topics: adversary-simulation, botnet, c2, hacking, onion, pentesting, red-team, remote-access, remote-control, tor, xena
- Language: Rust
- Homepage:
- Size: 254 KB
- Stars: 82
- Watchers: 0
- Forks: 9
- Open Issues: 0
-
Metadata Files:
- Readme: readme.md
- License: LICENSE
Awesome Lists containing this project
README
# INTRODUCTION
This is a command and control (C2) tool with communications over Tor network. Agent is made in Rust and C2 in Go.
C2 has two APIs; one for onion service listening on a unix socket, and another listening (by default) on port 8080 for connecting the user interface. C2's API for user interface integration is based on XENA's C2, offering a seemless integration with XENA's dark-themed, elegant user interface writen in Go, find out more at https://github.com/zarkones/XENA.
Agent does not need to "bundle" Tor service nor anything of a sort. Instead it relies on Arti, a rewrite of Tor in Rust. This allows easy compilation for many targets and way less trouble compared to trying to embed Tor writen in C into an agent. Arti does not offer all of the security features of legacy Tor implementation, however, that doesn't matter since you can (and should for the time being) run the onion service via the legacy battle tested Tor implementation.
Note that this is experimental and ongoing development effort.
### SOCIAL ###
[Patreon](https://www.patreon.com/zarkones) |
[Discord](https://discord.gg/qjJwSh2TF9) |
[X.com](https://x.com/zarkones) |
[YouTube](https://www.youtube.com/channel/UCn-7I-L-ZpiELb8-6z7z_Ug) |
[Itch.io](https://zarkones.itch.io) |
[GitHub](https://github.com/zarkones)
# FEATURES
- Tor integration (allows for end to end encryption, hiding the C2's IP address)
- Execution of shell commands.
- Basic attempt of hiding C2 config in the agent's binary.
- Registry based persistence on Windows.
- Shortcut takeover based persistence on Windows.
- Active hours, allowing an agent to communicate only within specific time frames.
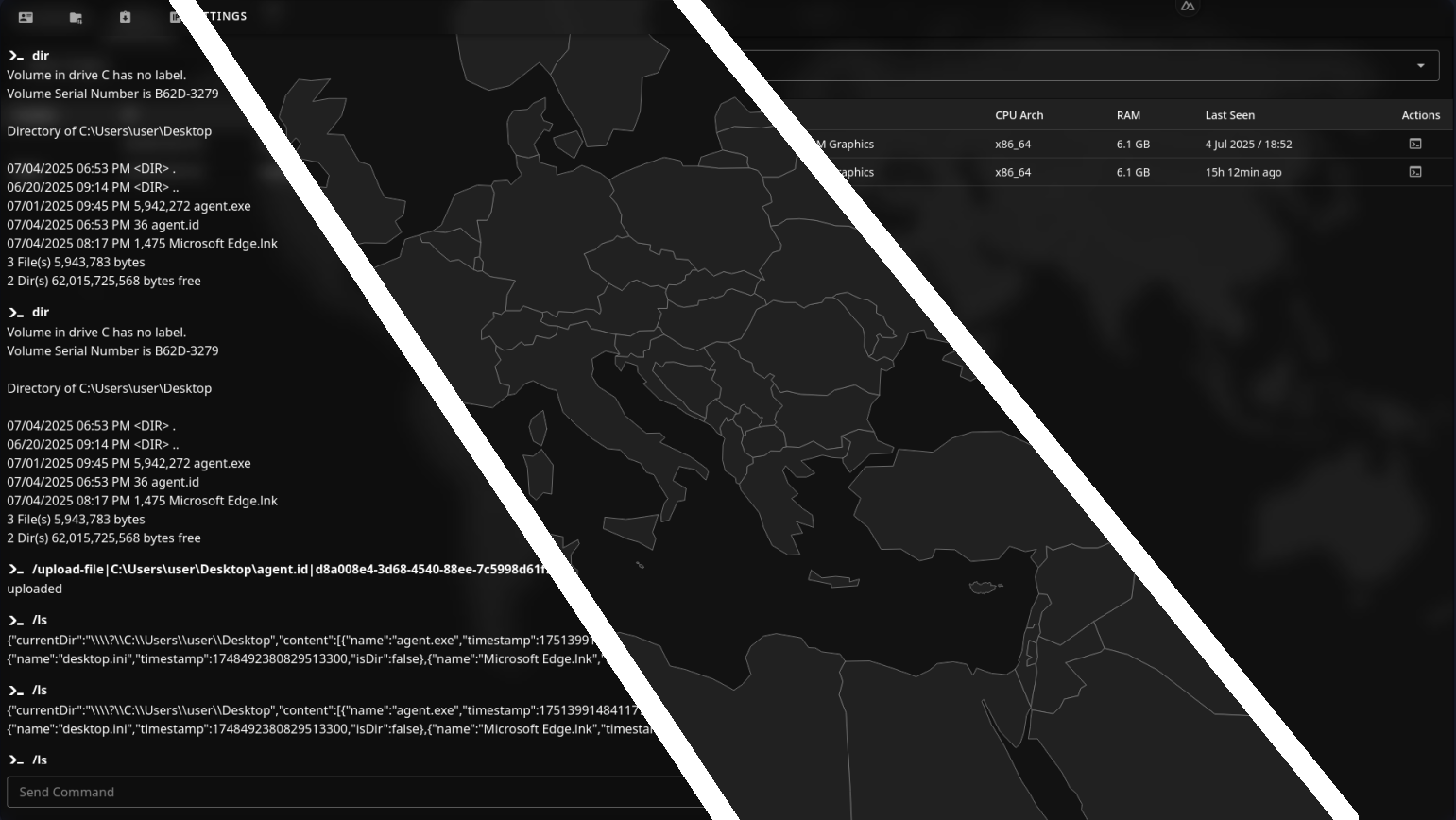
- Command "/system-details" makes an agent return information about CPU, RAM, networks, etc...
- Command "/find-files||" which based on criteria returns absolute path of files/directories of interest.
- Command "/upload-file|" which uploads a file via Tor.
- Command "/download-file|" which downloads a file via Tor.
- Command "/run|" which executes shell command without awaiting it.
- Command "/read-clipboard" which returns clipboard data.
Planned features:
- Sleep call acceleration detection.
- Optional hibernation mode.
- Take screenshot.
# SETUP
[Setup Video Tutorial](https://youtu.be/Q7xVNUWcgvM)
This guide assumes you have Go, Rust, and XENA ready.
- Run the C2 server via: cd api && go run . --api-key=your_secret_api_key_longer_than_16_chars
- Run XENA's user interface; go to settings tab and put your_secret_api_key_longer_than_16_chars into "Authentication Token" field. (Alternatively the UI accepts it via AUTH_TOKEN environment variable)
- Run Tor onion service based on the configuration made by the C2 program via: cd api && tor -f torrc
- When Tor onion service is ready you will see a .onion domain inside: api/onionservice/hostname, place that domain in function "get_address" in agent/src/config.rs
- Run the agent via: cd agent && cargo run
That's it. If you wish to know more about it execute the C2 server with "-h" command for help, or read the source code. It's a lean codebase. A good starting point for further development.