https://github.com/j3ssie/osmedeus
A Modern Orchestration Engine for Security
https://github.com/j3ssie/osmedeus
attack-surface-management bug-bounty bugbounty go hacking hacking-tool osint pentesting reconnaissance security security-tools workflow-engine workflows
Last synced: about 1 month ago
JSON representation
A Modern Orchestration Engine for Security
- Host: GitHub
- URL: https://github.com/j3ssie/osmedeus
- Owner: j3ssie
- License: mit
- Created: 2018-11-10T04:17:18.000Z (over 7 years ago)
- Default Branch: main
- Last Pushed: 2026-01-18T17:17:10.000Z (about 2 months ago)
- Last Synced: 2026-01-18T17:44:00.114Z (about 2 months ago)
- Topics: attack-surface-management, bug-bounty, bugbounty, go, hacking, hacking-tool, osint, pentesting, reconnaissance, security, security-tools, workflow-engine, workflows
- Language: Go
- Homepage: https://www.osmedeus.org/
- Size: 181 MB
- Stars: 6,028
- Watchers: 135
- Forks: 955
- Open Issues: 20
-
Metadata Files:
- Readme: README.md
- Funding: .github/FUNDING.yml
- License: LICENSE
Awesome Lists containing this project
- Awesome-OSINT-For-Everything - Osmedeus - Osmedeus is a Workflow Engine for Offensive Security. It was designed to build a foundation with the capability and flexibility that allows you to build your own reconnaissance system and run it on a large number of targets. (Recon)
- StarryDivineSky - j3ssie/osmedeus
- awesome-starts - j3ssie/osmedeus - A Workflow Engine for Offensive Security (security-tools)
- awesome-golang-repositories - osmedeus
- awesome-hacking-lists - j3ssie/osmedeus - A Workflow Engine for Offensive Security (Go)
README
# Osmedeus

Osmedeus - A Modern Orchestration Engine for Security
## What is Osmedeus?
[Osmedeus](https://www.osmedeus.org) is a security focused declarative orchestration engine that simplifies complex workflow automation into auditable YAML definitions, complete with encrypted data handling, secure credential management, and sandboxed execution.
Built for both beginners and experts, it delivers powerful, composable automation without sacrificing the integrity and safety of your infrastructure.
## Features
- **Declarative YAML Workflows** - Define reconnaissance pipelines using simple, readable YAML syntax
- **Two Workflow Types** - Modules for single execution units, Flows for multi-module orchestration
- **Multiple Runners** - Execute on local host, Docker containers, or remote machines via SSH
- **Distributed Execution** - Scale with Redis-based master-worker pattern for parallel scanning
- **Event-Driven Triggers** - Cron scheduling, file watching, and event-based workflow triggers with deduplication
- **Decision Routing** - Conditional workflow branching with switch/case syntax
- **Template Engine** - Powerful variable interpolation with built-in and custom variables
- **Utility Functions** - Rich function library with event generation, bulk processing, and JSON operations
- **REST API Server** - Manage and trigger workflows programmatically
- **Database Support** - SQLite (default) and PostgreSQL for asset tracking
- **Notifications** - Telegram bot and webhook integrations
- **Cloud Storage** - S3-compatible storage for artifact management
- **LLM Integration** - AI-powered workflow steps with chat completions and embeddings
See [Documentation Page](https://docs.osmedeus.org/) for more details.
## Installation
```bash
curl -sSL http://www.osmedeus.org/install.sh | bash
```
See [Quickstart](https://docs.osmedeus.org/quickstart/) for quick setup and [Installation](https://docs.osmedeus.org/installation/) for advanced configurations.
| CLI Usage | Web UI Assets | Workflow Visualization |
|-----------|--------------|-----------------|
| 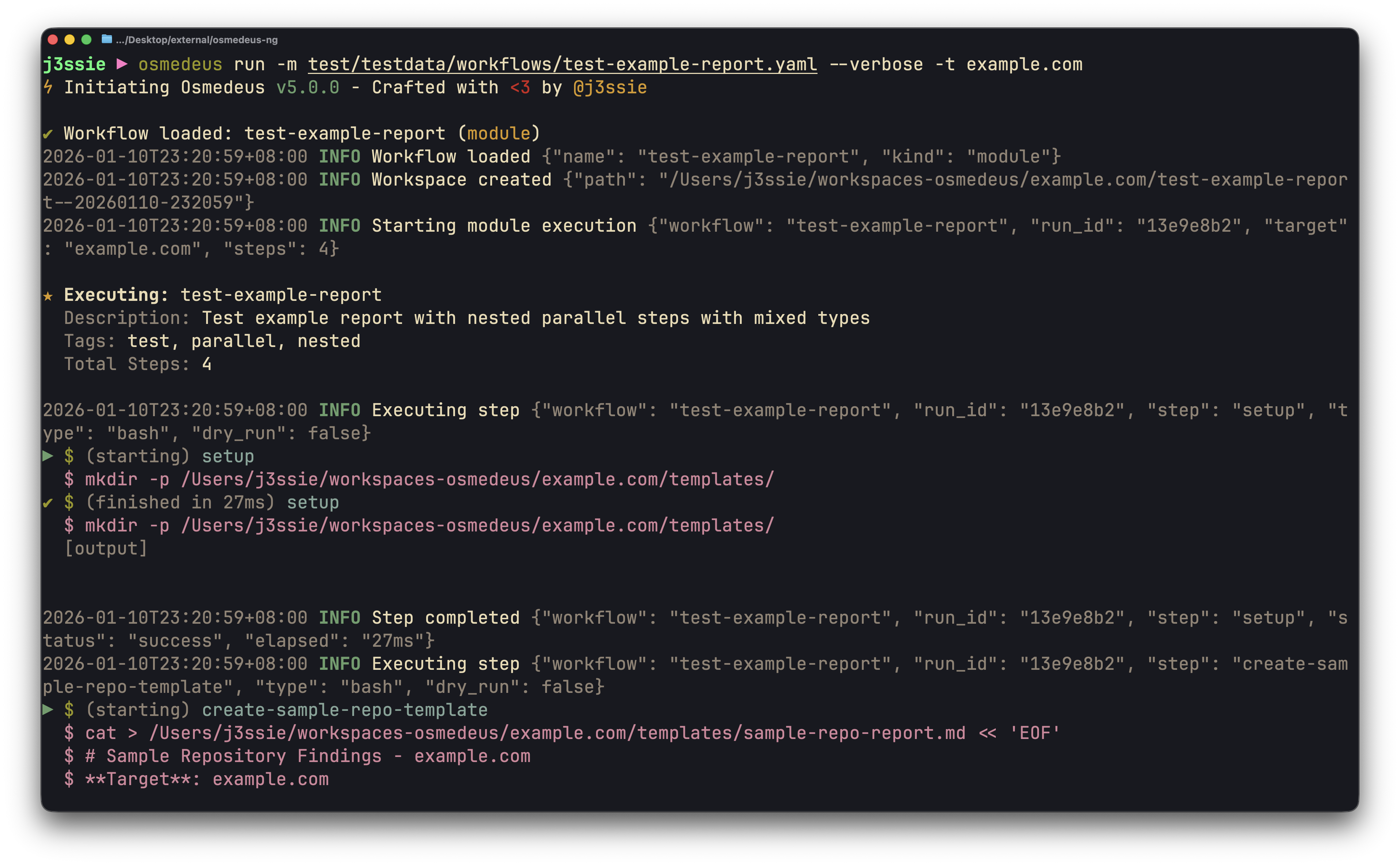 | 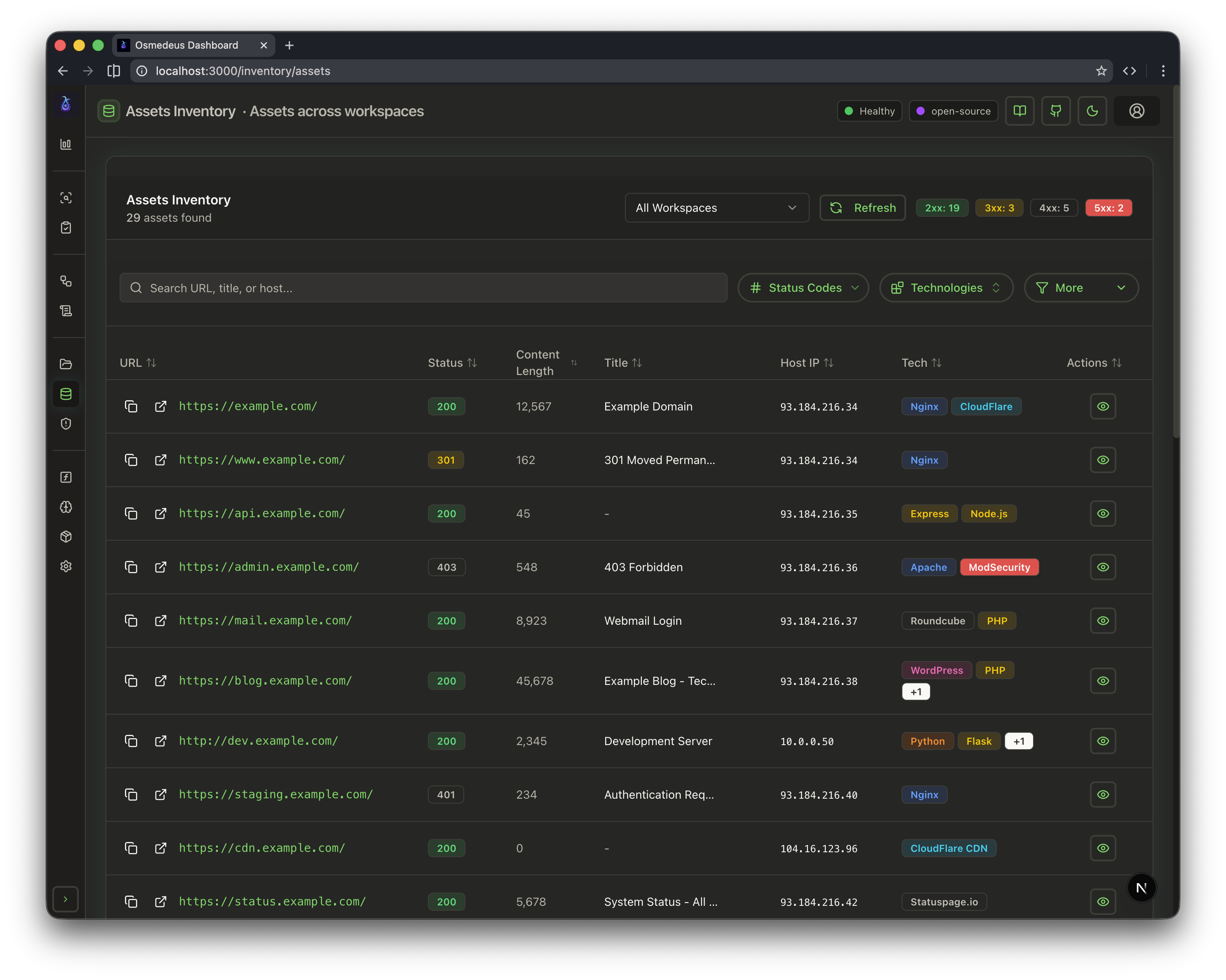 | 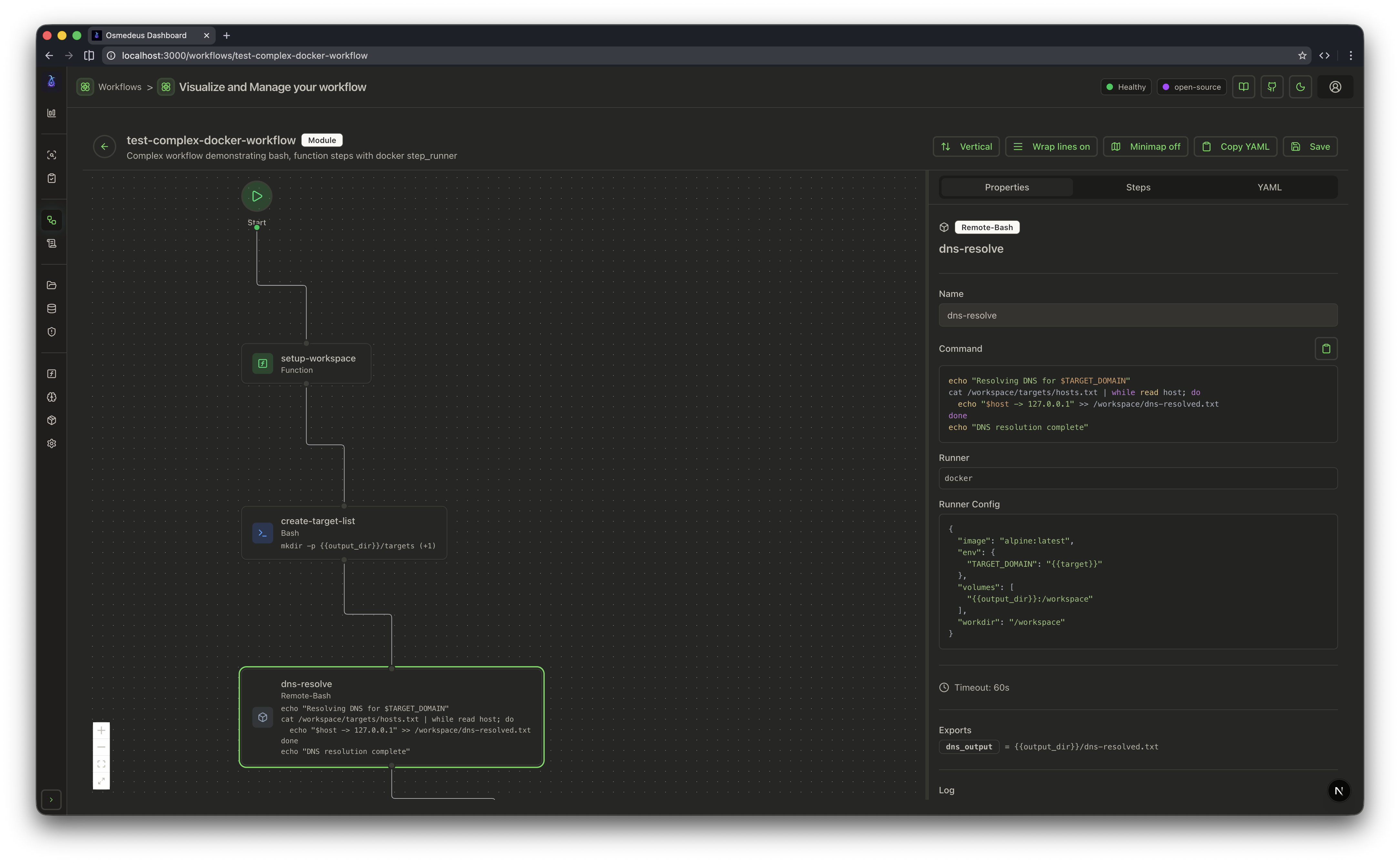 |
## Quick Start
```bash
# Run a module workflow
osmedeus run -m recon -t example.com
# Run a flow workflow
osmedeus run -f general -t example.com
# Multiple targets with concurrency
osmedeus run -m recon -T targets.txt -c 5
# Dry-run mode (preview)
osmedeus run -f general -t example.com --dry-run
# Start API server
osmedeus serve
# List available workflows
osmedeus workflow list
# Query database tables
osmedeus db list --table runs
osmedeus db list --table event_logs --search "nuclei"
# Evaluate utility functions
osmedeus func eval 'log_info("hello")'
osmedeus func eval -e 'httpGet("https://example.com")' -T targets.txt -c 10
# Show all usage examples
osmedeus --usage-example
```
## Docker
```bash
# Show help
docker run --rm j3ssie/osmedeus:latest --help
# Run a scan
docker run --rm -v $(pwd)/output:/root/workspaces-osmedeus \
j3ssie/osmedeus:latest run -f general -t example.com
```
For more CLI usage and example commands, refer to the [CLI Reference](https://docs.osmedeus.org/getting-started/cli).
## Core Components
### Trigger
| Type | Description | Use Case |
|------|-------------|----------|
| **Cron** | Schedule workflows at specific times | Regular scans |
| **File Watch** | Trigger workflows when files change | Continuous monitoring |
| **Event** | Trigger workflows based on external events | Integration with other tools |
| **Webhook** | Trigger workflows based on HTTP requests | External system integration |
| **Manual** | Trigger workflows manually via CLI or API | One-time tasks |
### Workflows
| Type | Description | Use Case |
|------|-------------|----------|
| **Module** | Single execution unit with sequential/parallel steps | Individual scanning tasks |
| **Flow** | Orchestrates multiple modules with dependencies | Complete reconnaissance pipelines |
### Runners
| Runner | Description |
|--------|-------------|
| **Host** | Local machine execution (default) |
| **Docker** | Container-based execution |
| **SSH** | Remote machine execution |
### Step Types
| Type | Description |
|------|-------------|
| `bash` | Execute shell commands |
| `function` | Call utility functions |
| `foreach` | Iterate over file contents |
| `parallel-steps` | Run multiple steps concurrently |
| `remote-bash` | Per-step Docker/SSH execution |
| `http` | Make HTTP requests |
| `llm` | AI-powered processing |
### Workflow Example
```yaml
kind: module
name: demo-bash
description: Demo bash steps with functions and exports
params:
- name: target
required: true
steps:
- name: setup
type: bash
command: mkdir -p {{Output}}/demo && echo "{{Target}}" > {{Output}}/demo/target.txt
exports:
target_file: "{{Output}}/demo/target.txt"
- name: run-parallel
type: bash
parallel_commands:
- 'echo "Thread 1: {{Target}}" >> {{Output}}/demo/results.txt'
- 'echo "Thread 2: {{Target}}" >> {{Output}}/demo/results.txt'
- name: check-result
type: function
function: 'fileLength("{{Output}}/demo/results.txt")'
exports:
line_count: "output"
- name: summary
type: bash
command: 'echo "Processed {{Target}} with {{line_count}} lines"'
```
For writing your first workflow, refer to the [Workflow Overview](https://docs.osmedeus.org/workflows/overview).
## Roadmap and Status
The high-level ambitious plan for the project, in order:
| # | Step | Status |
| :-: | ----------------------------------------------------------------------------- | :----: |
| 1 | Osmedeus Engine reforged with a next-generation architecture | ✅ |
| 2 | Flexible workflows and step types | ✅ |
| 3 | Event-driven architectural model and the different trigger event categories | ✅ |
| 4 | Beautiful UI for visualize results and workflow diagram | ✅ |
| 5 | Rewriting the workflow to adapt to new architecture and syntax | ⚠️ |
| 6 | Testing more utility functions like notifications | ⚠️ |
| 7 | Generate diff reports showing new/removed/unchanged assets between runs. | ❌ |
| 8 | Adding step type from cloud provider that can be run via serverless | ❌ |
| N | Fancy features (to be discussed later) | ❌ |
## Documentation
| Topic | Link |
|----------------------|----------------------------------------------------------------------------------------------------------|
| Getting Started | [docs.osmedeus.org/getting-started](https://docs.osmedeus.org/getting-started) |
| CLI Usage & Examples | [docs.osmedeus.org/getting-started/cli](https://docs.osmedeus.org/getting-started/cli) |
| Writing Workflows | [docs.osmedeus.org/workflows/overview](https://docs.osmedeus.org/workflows/overview) |
| Event-Driven Triggers| [docs.osmedeus.org/advanced/event-driven](https://docs.osmedeus.org/advanced/event-driven) |
| Deployment | [docs.osmedeus.org/deployment](https://docs.osmedeus.org/deployment) |
| Architecture | [docs.osmedeus.org/concepts/architecture](https://docs.osmedeus.org/concepts/architecture) |
| Development | [docs.osmedeus.org/development](https://docs.osmedeus.org/development) and [HACKING.md](HACKING.md) |
| Extending Osmedeus | [docs.osmedeus.org/development/extending-osmedeus](https://docs.osmedeus.org/development/extending-osmedeus) |
| Full Documentation | [docs.osmedeus.org](https://docs.osmedeus.org) |
## License
Osmedeus is made with ♥ by [@j3ssie](https://twitter.com/j3ssie) and it is released under the MIT license.




